DevtiGroup Solutions Strengthens its Data Security Protocols to Ensure Maximum Protection
Publié le 25 March 2025
🛡️ In an increasingly digital environment exposed to the risks of cyberattacks, DevtiGroup Solutions has taken the initiative to strengthen its security protocols to ensure optimal protection of its clients' sensitive data. This decision is part of a context where the protection of personal data has become an absolute priority for both businesses and individuals. In the face of growing digital threats, this proactive approach is crucial to ensure the confidentiality and availability of information.

⚠️ The Need for Strengthened Data Security in a Tense Digital Environment
Today, every business, regardless of its size or sector, faces growing challenges in data security. Cybercriminals continue to refine their techniques, jeopardizing the confidentiality of sensitive information. In the age of Big Data and artificial intelligence, the volume of generated data keeps increasing, making cyberattacks more frequent and sophisticated. Businesses must therefore intensify their efforts to protect against data leaks, hacks, and ransomware attacks.
DevtiGroup Solutions fully recognizes these challenges and is committed to addressing the imperative need to secure its clients' sensitive data. The company is dedicated to staying at the forefront of technology in information security, which is a cornerstone of its trust strategy with clients.
🔐 Enhanced Security Protocols by DevtiGroup Solutions
DevtiGroup Solutions has implemented a series of advanced security protocols to ensure maximum protection of sensitive data, whether stored or in transit. These measures, combining cutting-edge technology with rigorous access management, aim to meet the strictest security requirements and ensure continuous protection against potential threats.
🧊 Data Encryption: A Shield Against Sensitive Information Leaks
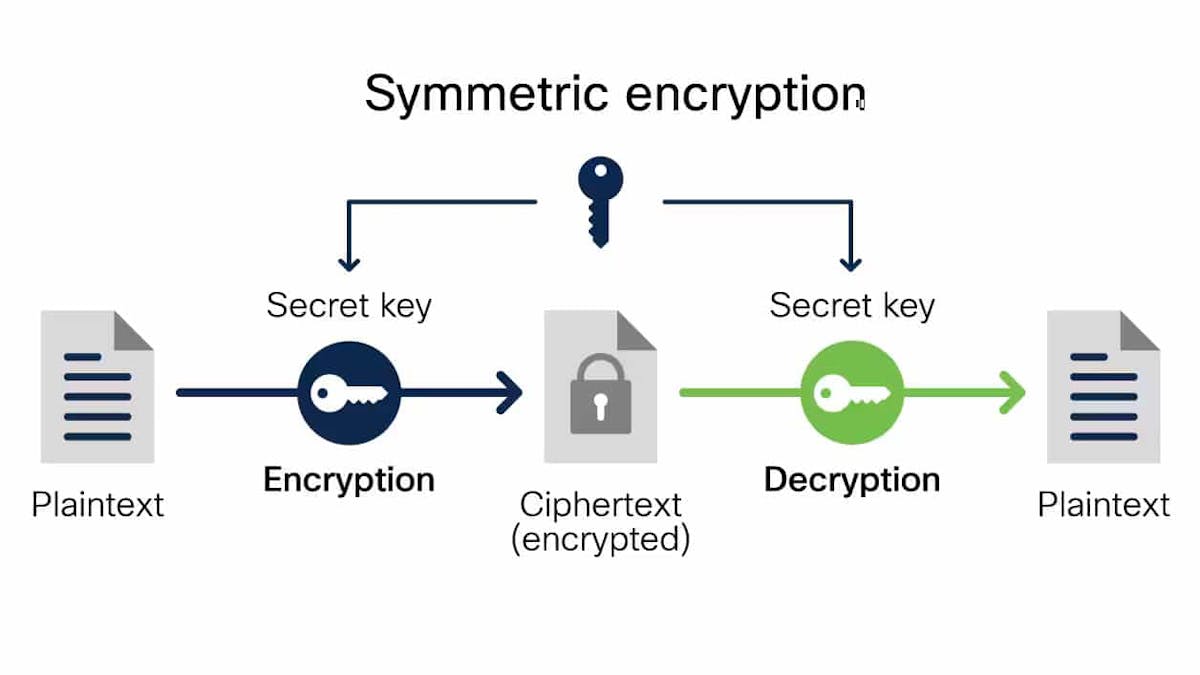
Data encryption is one of the cornerstones of the security measures implemented by DevtiGroup Solutions. Encryption transforms sensitive information into an unreadable format for anyone not authorized to access it, ensuring the security of data exchanges at every stage of their lifecycle. Whether for data in transit or at rest, encryption ensures that information is protected against malicious interception.
The AES (Advanced Encryption Standard) encryption, one of the most secure available today, is used to ensure maximum data protection. With this technology, even in the case of unauthorized access to systems, the information remains inaccessible and unusable.
🔐 Strict Access Controls: Data Access Reserved for Authorized Individuals
Access control management is another key aspect of DevtiGroup Solutions' security strategy. Businesses must be able to control and restrict access to sensitive data to prevent unauthorized attempts or intrusions. To this end, DevtiGroup Solutions implements a strict access control system based on the principle of least privilege.
This ensures that only users with a legitimate need to access the information can do so. Additionally, all access is subject to multi-factor authentication (MFA), which adds an extra layer of security to protect accounts from any attempt at impersonation.
🧠 Continuous Monitoring and Anomaly Detection: Artificial Intelligence for Security
In addition to traditional security protocols, DevtiGroup Solutions integrates AI-based monitoring systems to detect any suspicious activity or intrusion attempts. These systems are designed to analyze user behavior in real time and identify anomalies that could signal an attempt at hacking or fraud.
Thanks to advanced machine learning algorithms and anomaly detection techniques, DevtiGroup Solutions is able to quickly detect unauthorized access attempts and respond proactively to protect sensitive data.

📋 Security Audits and Compliance with International Standards
Compliance with international data security standards, such as the GDPR (General Data Protection Regulation), is a strategic priority for DevtiGroup Solutions. In addition to technical measures, regular audits are conducted to ensure that all data management practices strictly adhere to the applicable laws. These audits not only help detect potential vulnerabilities in security systems but also ensure continuous updates to data management processes.
These regular checks allow the company to stay aligned with industry best practices and reassure its clients that their data is being managed with the highest level of security.

🏢 A Fully Reliable Management of Outsourced Processes
Thanks to these enhanced security measures, DevtiGroup Solutions ensures a completely reliable and secure management of outsourced processes. Companies that entrust their processes to DevtiGroup Solutions can enjoy complete peace of mind, knowing that their data is protected by the most robust protocols.
This trust is even more important in a context where more and more companies are outsourcing critical functions such as customer service, IT, or even human resources management. Being able to rely on a company like DevtiGroup Solutions, which takes data protection seriously, gives clients the certainty that their information is in good hands.
🤝 Data Security at the Heart of Trust Strategy
DevtiGroup Solutions sees data security as a fundamental element of its relationship with its clients. By continually strengthening its security protocols, the company is committed to offering maximum protection and maintaining an optimal level of trust. This strategy is especially crucial in an environment where cybersecurity is more than ever a factor of competitiveness and a guarantee of reliability.
🏁 Conclusion: Toward Total Security for Sensitive Data
DevtiGroup Solutions has implemented:
🔒 Advanced encryption
🔐 Strict access controls
📋 Regular security audits
🧠 Intelligent real-time monitoring
With full compliance with GDPR, DevtiGroup ensures complete peace of mind for its clients, regardless of their industry.
🚀 By creating a secure environment for outsourcing, DevtiGroup Solutions positions itself as a leader in sensitive data protection.
